Cyber security standards for small-medium businesses
Small-medium businesses are seriously at-risk of cyber threats as reported in the latest Australian Cyber Security Centre Threat Report 2024-2025.
84,700
cybercrime reports made in 2024-2025 to ReportCyber (Australian Cyber Security Centre).
$97,166
average reported loss for Australian medium-sized businesses (up 55% on previous year).*
every 6 minutes
a cybercrime is reported in Australia.
38%
of incidents involved phishing tactics making this the No. 1 approach used by cyber criminals, with this tactic even higher in government incidents (52%).
$84,000,000
total national self-reported loss in 2023-2024.**
Source: Australian Cyber Security Centre Annual Cyber Threat Report (2024-2025)
*Medium-sized businesses (defined by Australian Bureau of Statistics as between 20 and 199 employees).
** Australian Cyber Security Centre did not report on this statitics in 2024-2025.
Australian Cyber Security Centre’s Essential Eight
Australian Cyber Security Centre (ACSC), based within the Australian Signals Directorate (ASD), has published a useful set of online resources that discuss the controls to put in place to keep your organisation secure.
While no set of mitigation strategies are guaranteed to protect against all cyber threats, organisations are recommended to implement eight essential mitigation strategies from the ACSC’s Strategies to Mitigate Cyber Security Incidents as a baseline.
This baseline, known as the Essential Eight, focuses on making the work required for adversaries to compromise systems much harder.
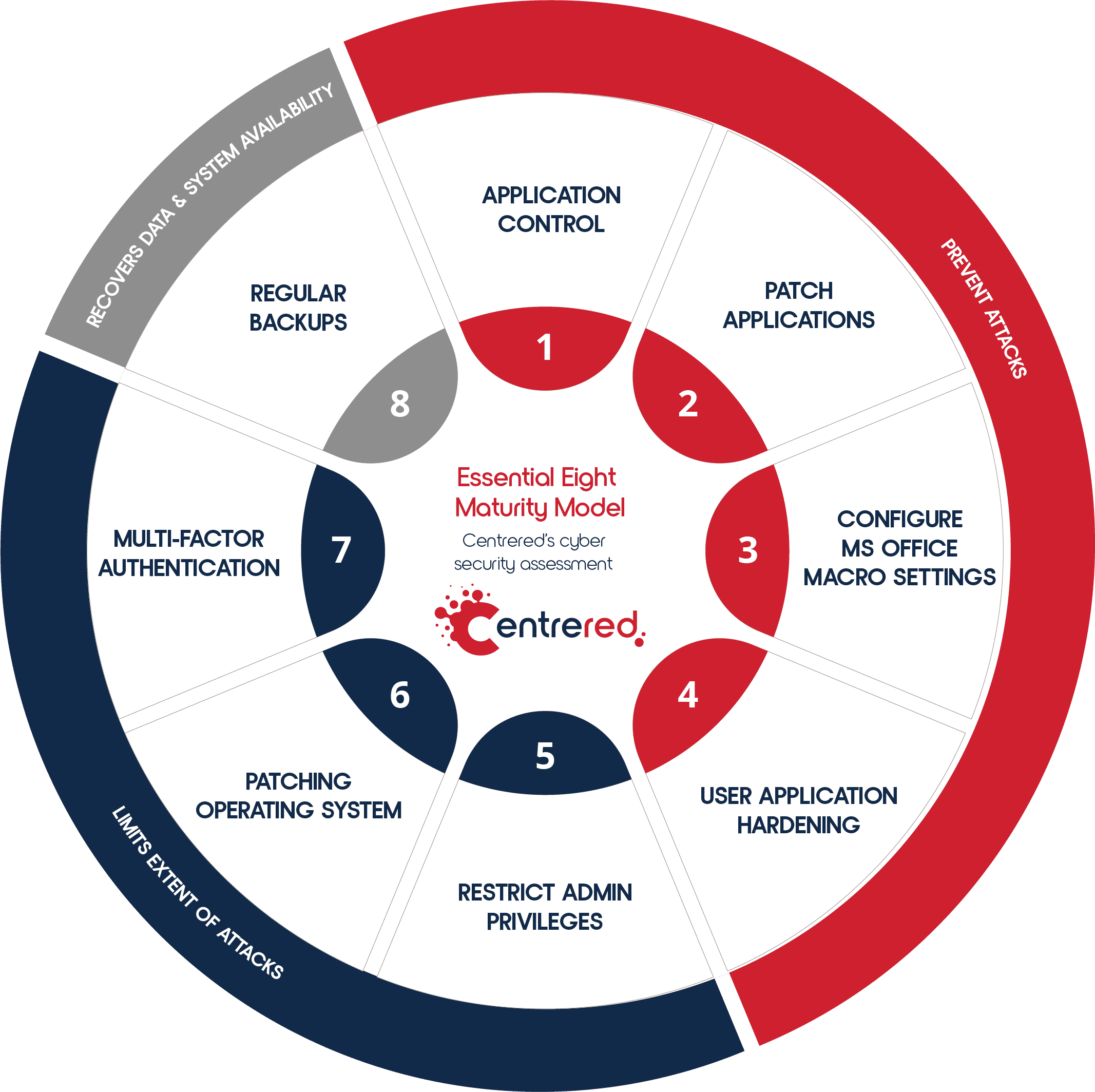
There are eight areas where mitigations should be developed to help keep your organisation safe (see Figure 1) including:
- Application Control
- Patch Applications
- Configure MS Office Macro Settings
- User Application Hardening
- Restrict Admin Privileges
- Patching Operating System
- Multi-factor Authentication
- Regular Backups
While the Essential Eight can help to mitigate most cyber threats, it will not mitigate all cyber threats. Proactively implementing measures to increase maturity around the Essential Eight can be time and resource intensive, however it is often less time and resource intensive than having to respond to a large-scale cyber security incident which could cause significant impact to your business concerns.
Figure 1 Centrered Essential Eight Maturity Model
Our Proposal
Centrered will conduct an in-depth discovery across your IT Environment to establish how your organisation currently aligns with the ACSC Essential Eight Maturity Level One.
Upon completion of the discovery, Centrered will provide a report detailing where your organisation aligns with the Essential Eight. The report will provide you with an easy to understand controls assessment that will highlight the areas of Essential 8 that are covered, partially covered or not covered within your organisation. Click on Figure 2 to view a sample report.
The report will also detail any recommendations for your organisation to take into consideration to fully comply with Essential Eight.
Benefits
- Clarity on your organisation’s alignment with Australian Cyber Security Centre guidelines.
- Know what you need to do to reduce the risk of successful cyber attacks.
- Have a clear report that informs you and your stakeholders.
- Have information to make informed business investment decisions to increase your cyber security posture.
Figure 2 Example of Centrered Standards Coverage Report
Get in contact with us
Register your interest by completing the contact form below or call our Sales Team on 6239 4222. Our existing ICT partners can contact their Customer Success Manager to learn more.